week7-re-ISCC
something
先die查壳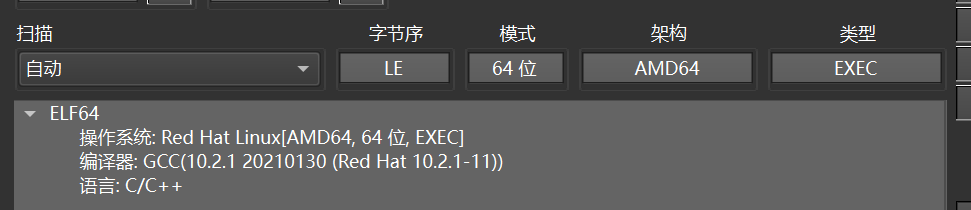
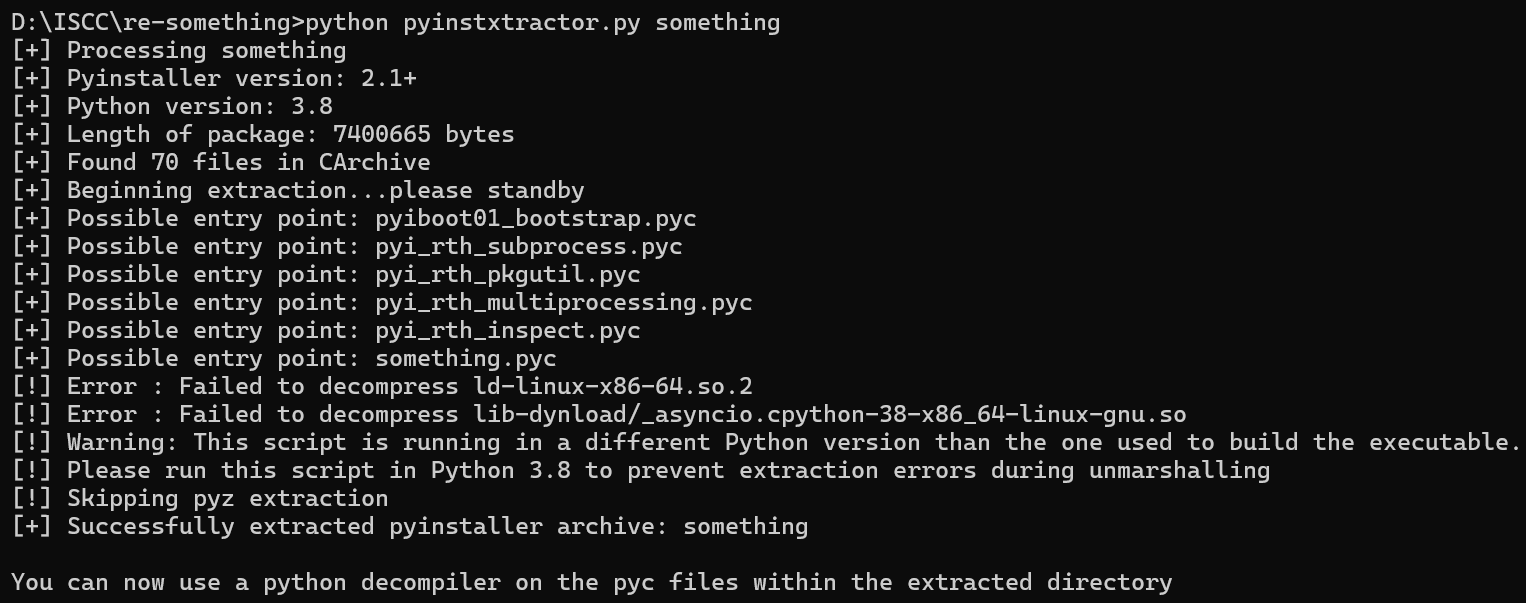
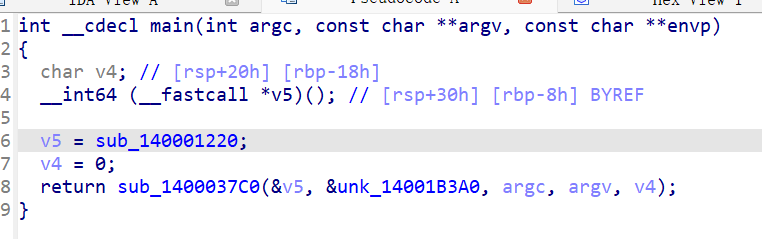
用ida打开后,直接进入main函数,看到与pyinstaller有关,利用python反编译一下(需要在同一目录下)
这个题不会啊
冗余的代码
依旧是先查壳
拖进ida
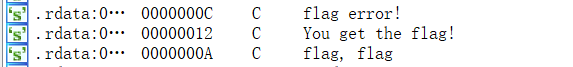
shift+f12看一下 关键字,看到下面的部分,猜测可能是与flag有关,跟进看看
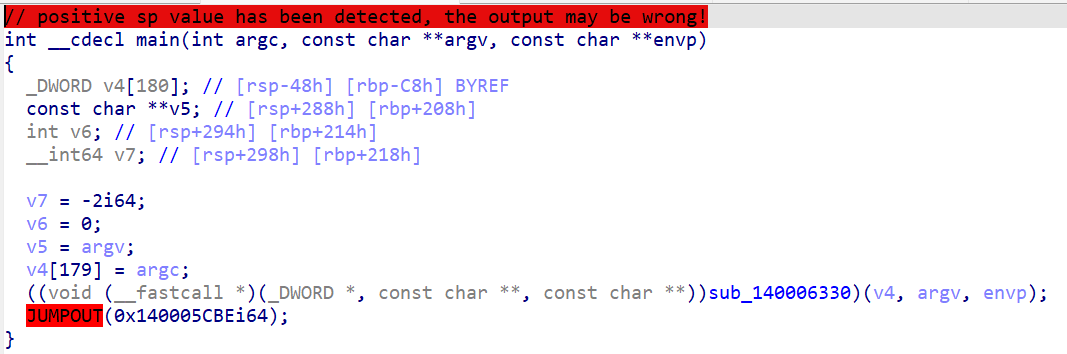
看到爆红的部分,可能是花指令,去除一下,nop掉,按C编译
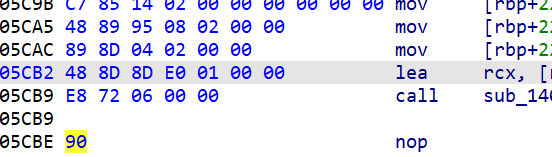
一个接着一个,本来想数一下的,但是太多了,没数过来,我们把他们全部nop掉就行了
方法一:
重新看一下关键字,依旧是刚才那个地方 跟进一下,看到那个部分的函数,试一下动调
目前没有成功
方法二:
看wp中写的,直接利用idapython一把梭,先把代码放上,再看看逻辑
1 | import struct |
这段代码涉及XXTEA,结合xor异或操作,最终生成字符串(也就是flag)
- 从这个文件中读取16字节密钥
- 使用 XXTEA 算法 加密给定的整数数组
v = [33686020, 67174660, 67240450] - 对加密后的数据再进行 逐字节 XOR 操作
- 将结果转换为十六进制格式,拼接成
ISCC{...}形式的字符串。
运行后直接得到flag
faze
依旧是先查壳
拖进ida中,直接查看一下关键字
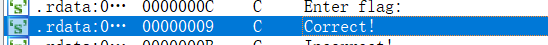
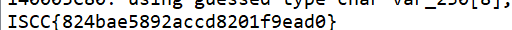
我们发现这个flag是自己输入的,我们可以用动调解决类似题目,我们先跟进这段,进入这段代码
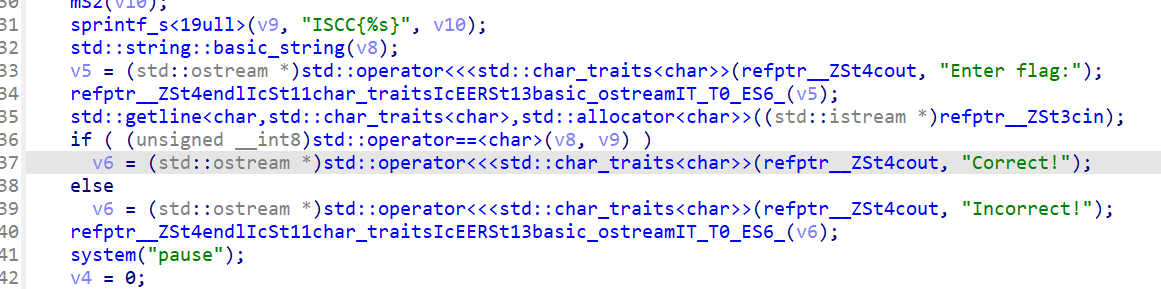
我们在correct这里和incorrect都下一个断点
随便输入flag后我们就直接得到了flag

ISCC{(O[&TR\7@ye@}
SecretGird
依旧是先查壳
拖进ida中
我想调试一下,出现下面的问题
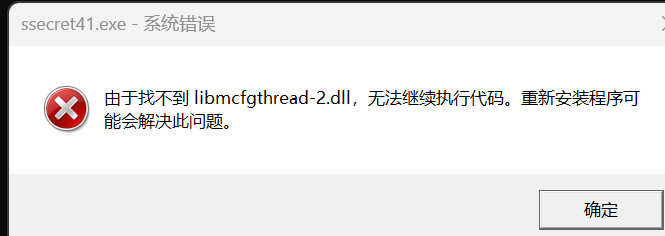
出现和wp中一样的问题
解决好后重新来一遍
我们看到main函数中
调用 checklist1() 判断输入格式是否合格。
- 不合格直接提示“Invalid format”。
如果合格,则调用 checklist2() 评分。
- 如果得分 > 4,显示鼓励信息并显示 flag。
- 否则提示失败。
看一下这两段函数的具体内容
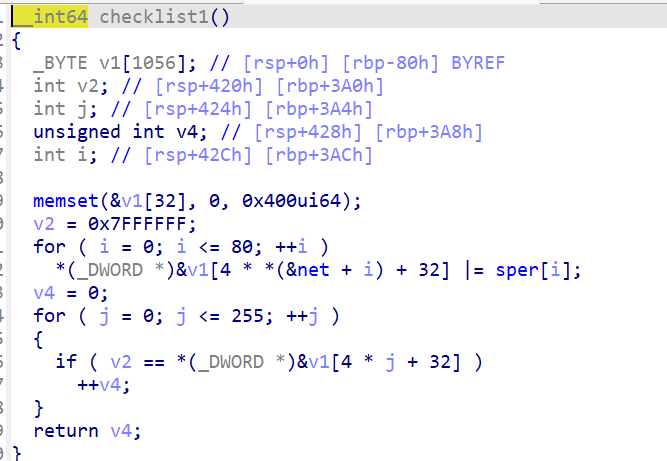
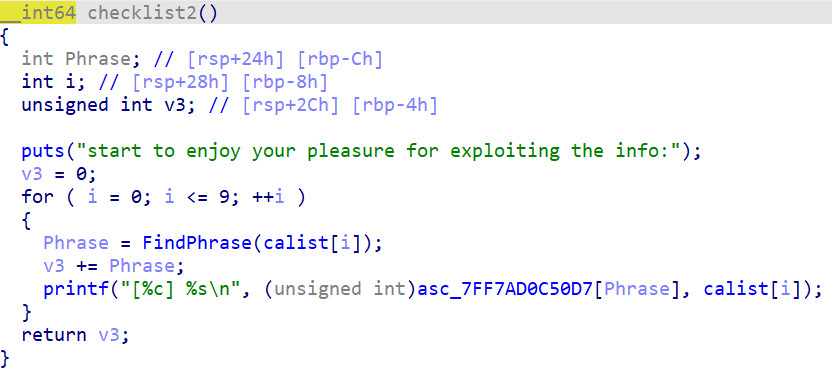
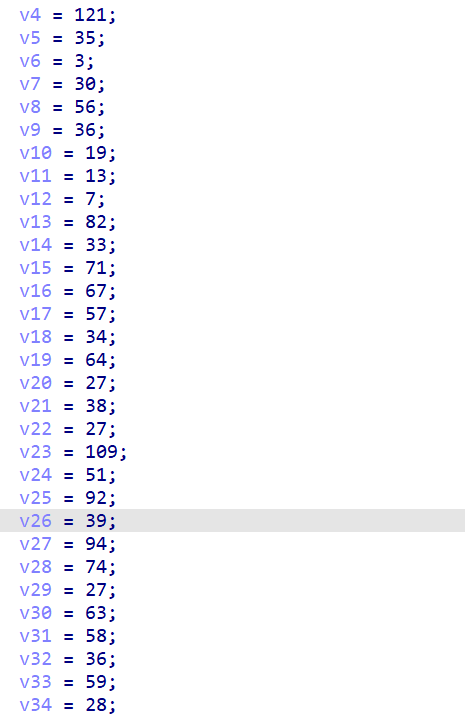
calist中 是数独填写内容
我们看一下printflag函数
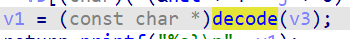
里面有密文
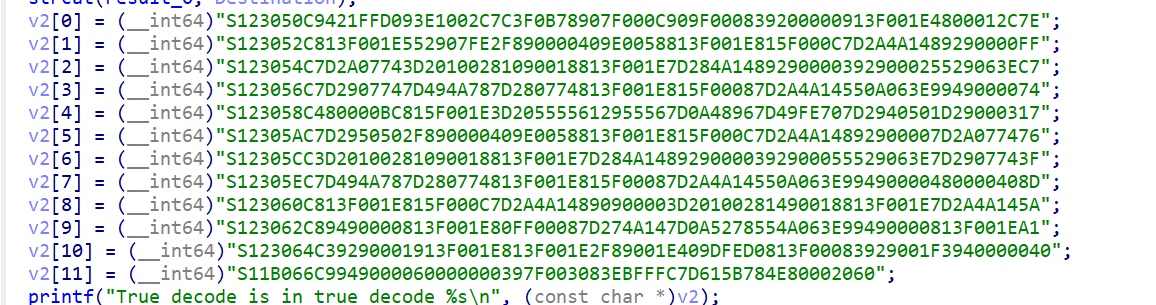
提取解密
1 | v2[0] ="S12305C9421FFD093E1002C7C3F0B78907F000C909F00083920000913F001E4800012C7E"; |
这里就直接使用wp中的脚本了····
1 | from capstone import * |
运行后看到汇编代码
1 | D:\PyCharmProjects\aaa\.venv\Scripts\python.exe "C:\Users\Lenovo\Documents\WeChat Files\wxid_ummbals4orzj22\FileStorage\File\2025-05\123.py" |
依照这个逻辑再写一个python脚本
1 | def encrypt(input_data, output): |
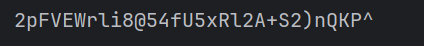
运行出结果,加上ISCC{}
就是flag了
greeting
先查壳
找一下main函数
跟进v5,看到有爆红的部分,去花,别忘了按C编译一下
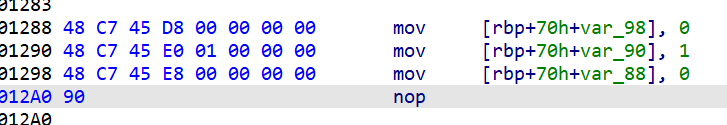
类似如上
重新看一下main函数,还有爆红的部分,那就继续上面的操作
操作完成后,再看一下main函数
找到 加密前的明文,对应的密文就在内存中被读取并解密成 xmmword_14001B390
找到使这段代码生成 xmmword_14001B390 的 v30[i]
那我们就跟进这个函数
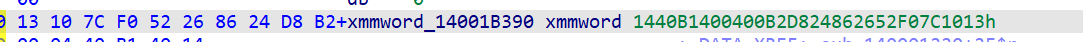
看到密文
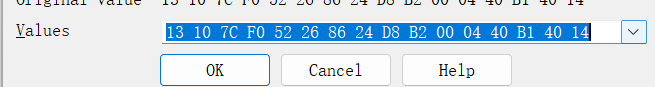
1 | def ror8(val, shift): |
当然,也可以转成hex后面用赛博厨子也可以
1 | def ror8(val, shift): |
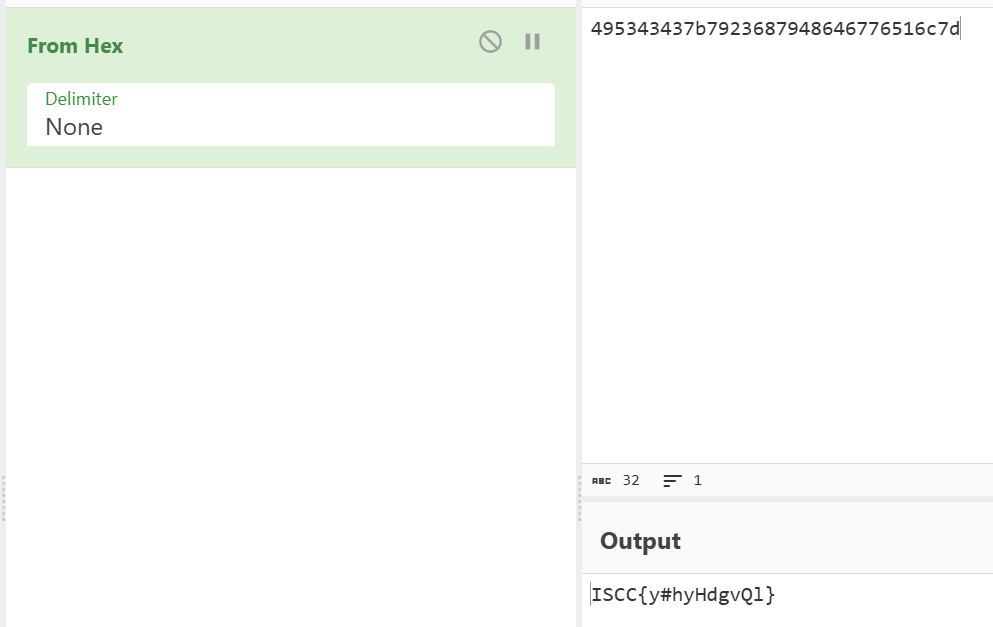
再看一下上面的代码的逻辑
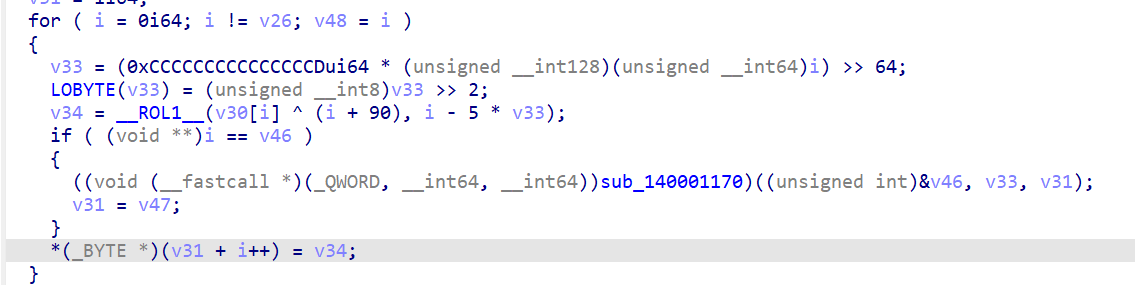
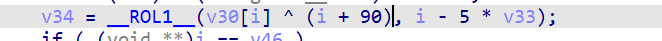
si128是目标明文
有趣的小游戏
CrackMe
方法一:
先查壳
看一下关键函数
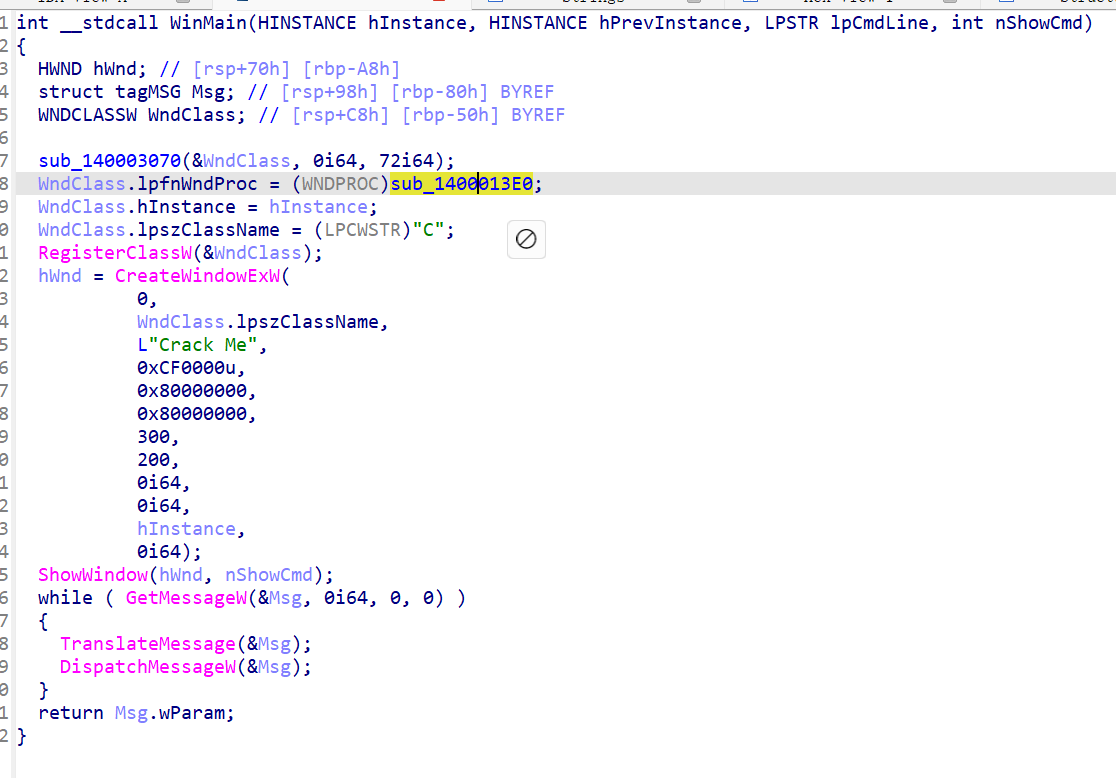
跟进黄色部分,进去之后tap,修复一下函数表
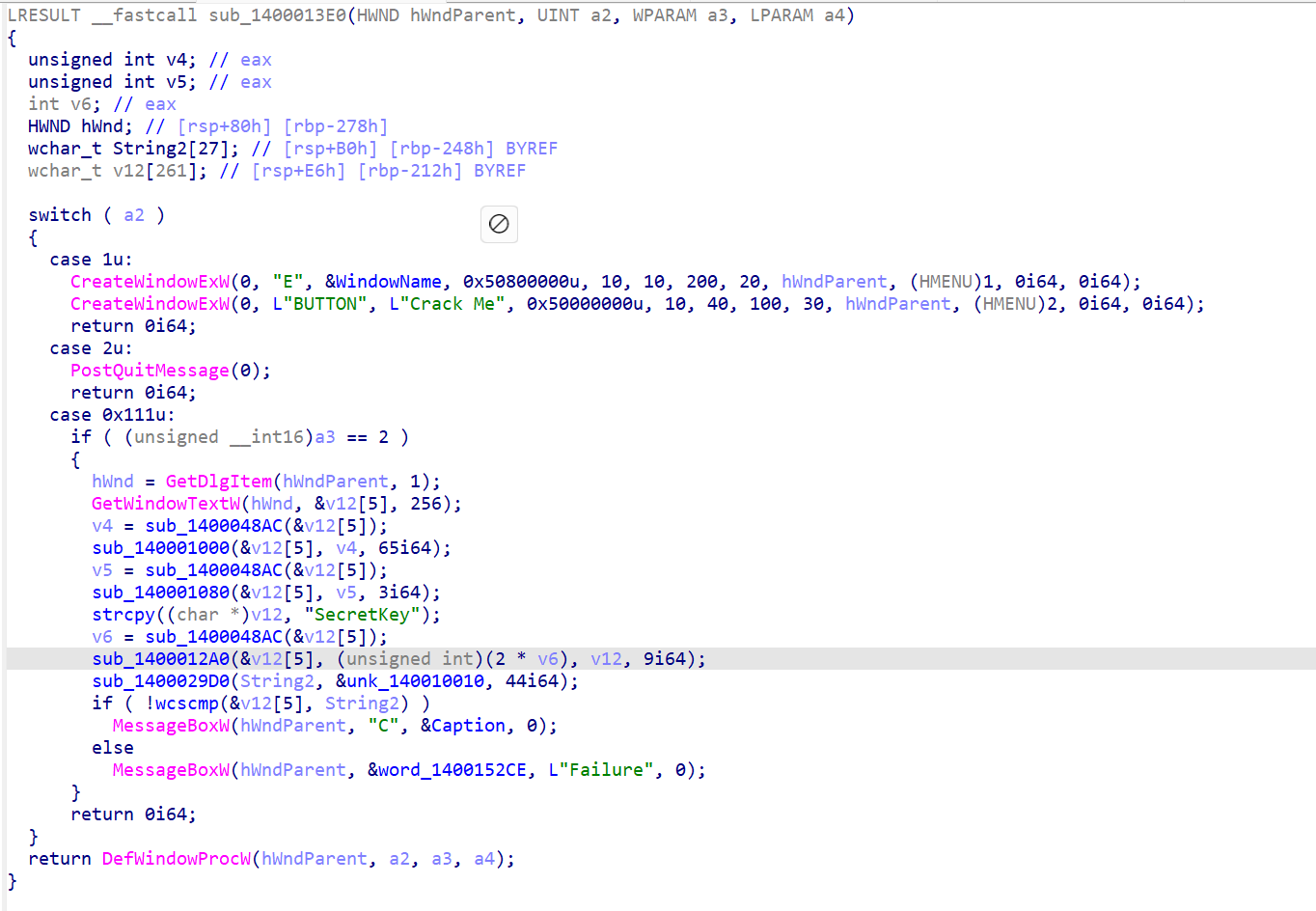
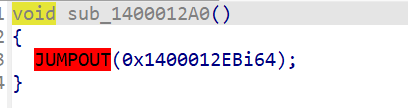
进去nop掉
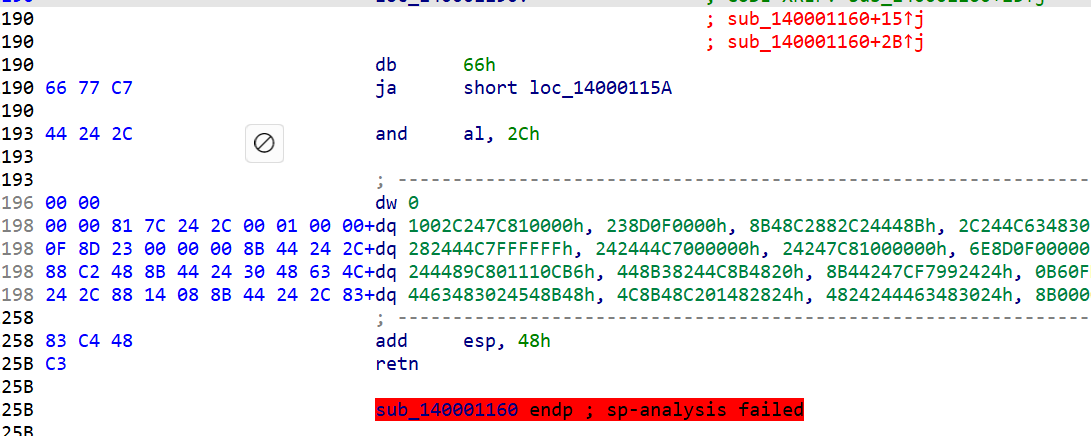
去完以后,提取数据
上面看到密钥是SecretKey
1 | from Crypto.Cipher import ARC4 |
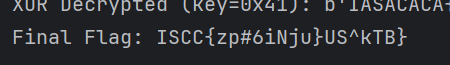
ISCC{zp#6iNju}US^kTB}
方法二:
idapython脚本一把梭
1 | from ida_bytes import * |
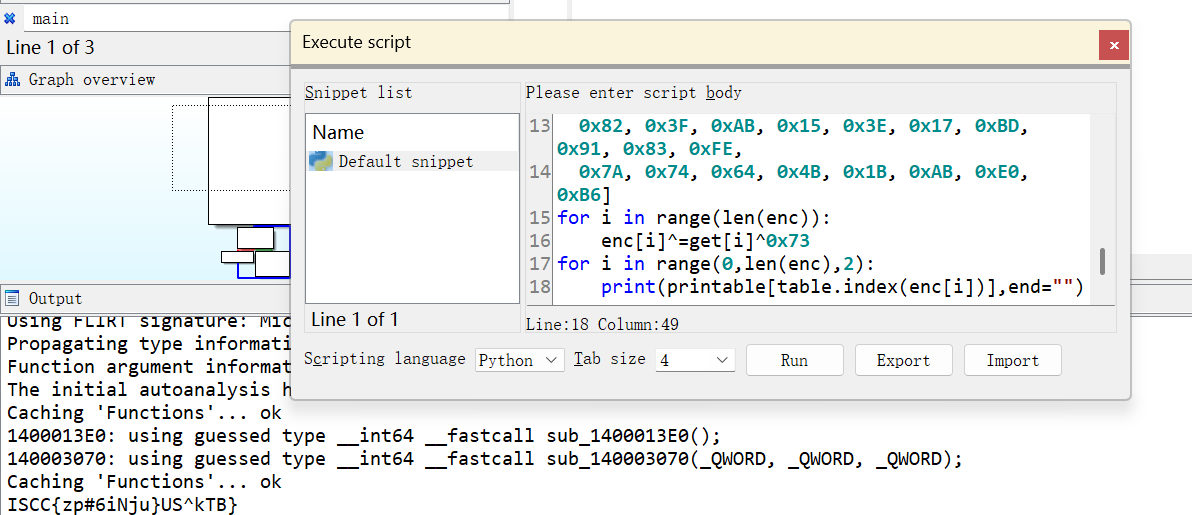
运行得到flag
我们看一下逻辑
解密混淆数据,使用xor异或和查表替换还原原始数据
- 读取加密数据
- 用
get数组和0x73进行xor解密 - 每两个字节取第1字节
- 用
printable映射到最终字符,输出结果
uglyCpp
先查壳
直接看一下main函数,看一下
看到有一段奇怪的字符,可能是密文,也就是黄色部分,跟进看一下
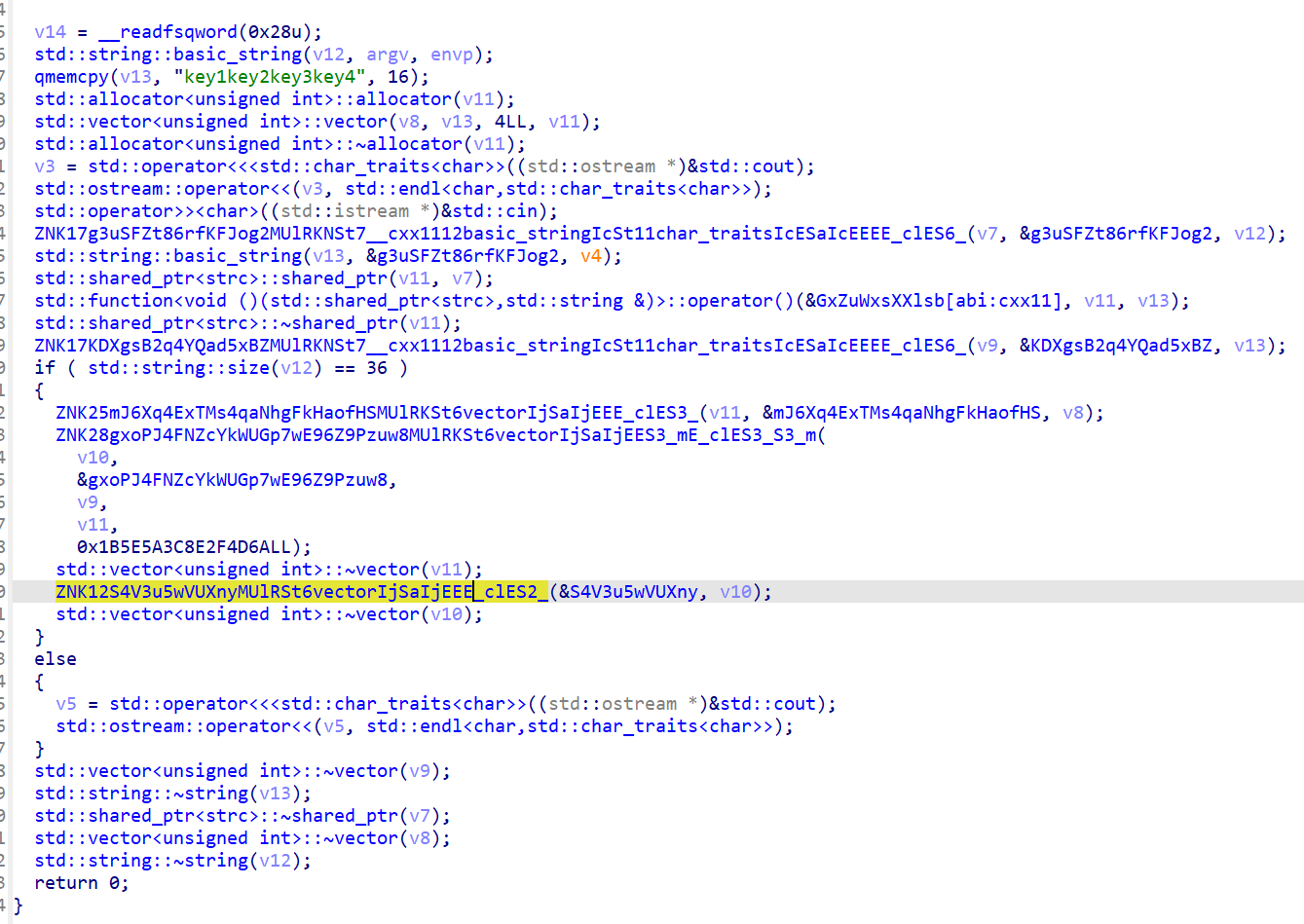
看到密文
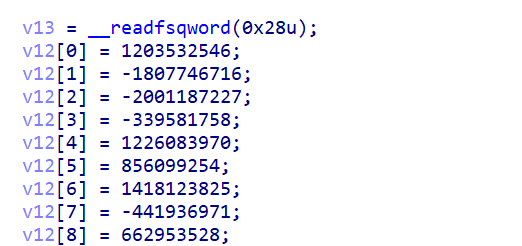
提取一下其中的数据
1 | v12[0] = 1203532546; // 0x47C2B102 |
写解密脚本
1 | v = [1203532546,-1807746716,-2001187227,-339581758,1226083970,856099254,1418123825,-441936971,662953528]#密文 |
看一下脚本的逻辑
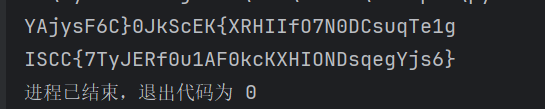
ISCC{7TyJERf0u1AF0kcKXHIONDsqegYjs6}
xor运算和查表替换,还原出最终的flag字符串