re10
EQUATION
先查壳
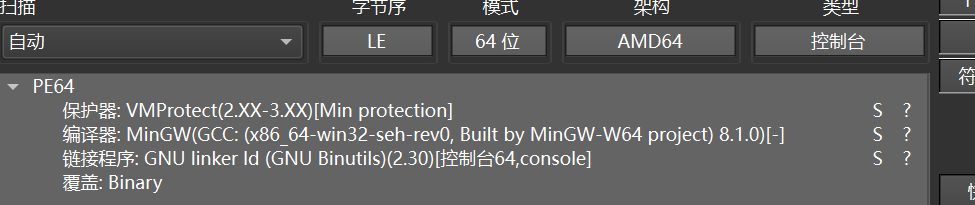
拖进ida,查看一下main函数
这个函数非常长
这个是Z3约束求解,数据都在if语句条件下,都成立的情况下,就是flag
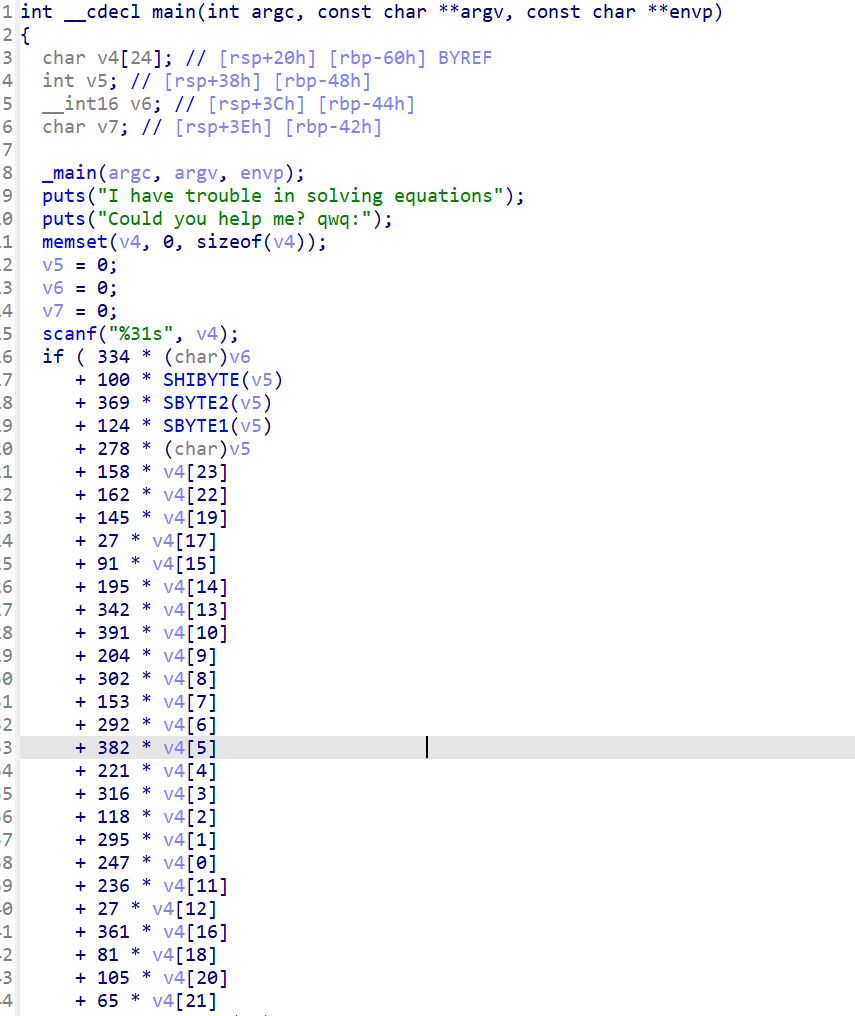
在其中每一个||,都代表一个独立方程,一共是31个
我们假设已知前缀为moectf{
1 | from z3 import * |
junk_code
这道题考的主要是花指令
先查壳
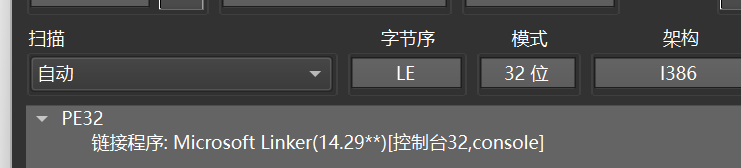
拖进去,看一下main函数
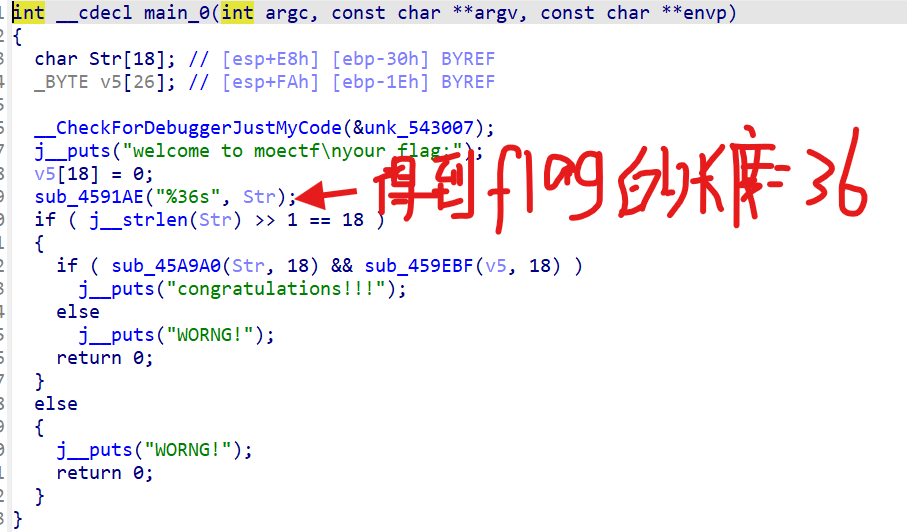
if判断长度是否满足36,再一个if判断是否满足俩个条件,满足就输出congratulation。
跟进一下两个判断函数,其实在这里差不多能猜出来flag是由两部分构成
分别十八个字节
这两个
发现里面爆红了
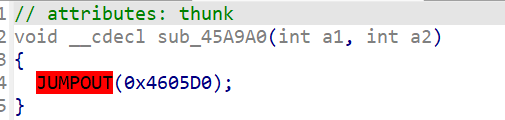
跟进,发现反编译出了问题
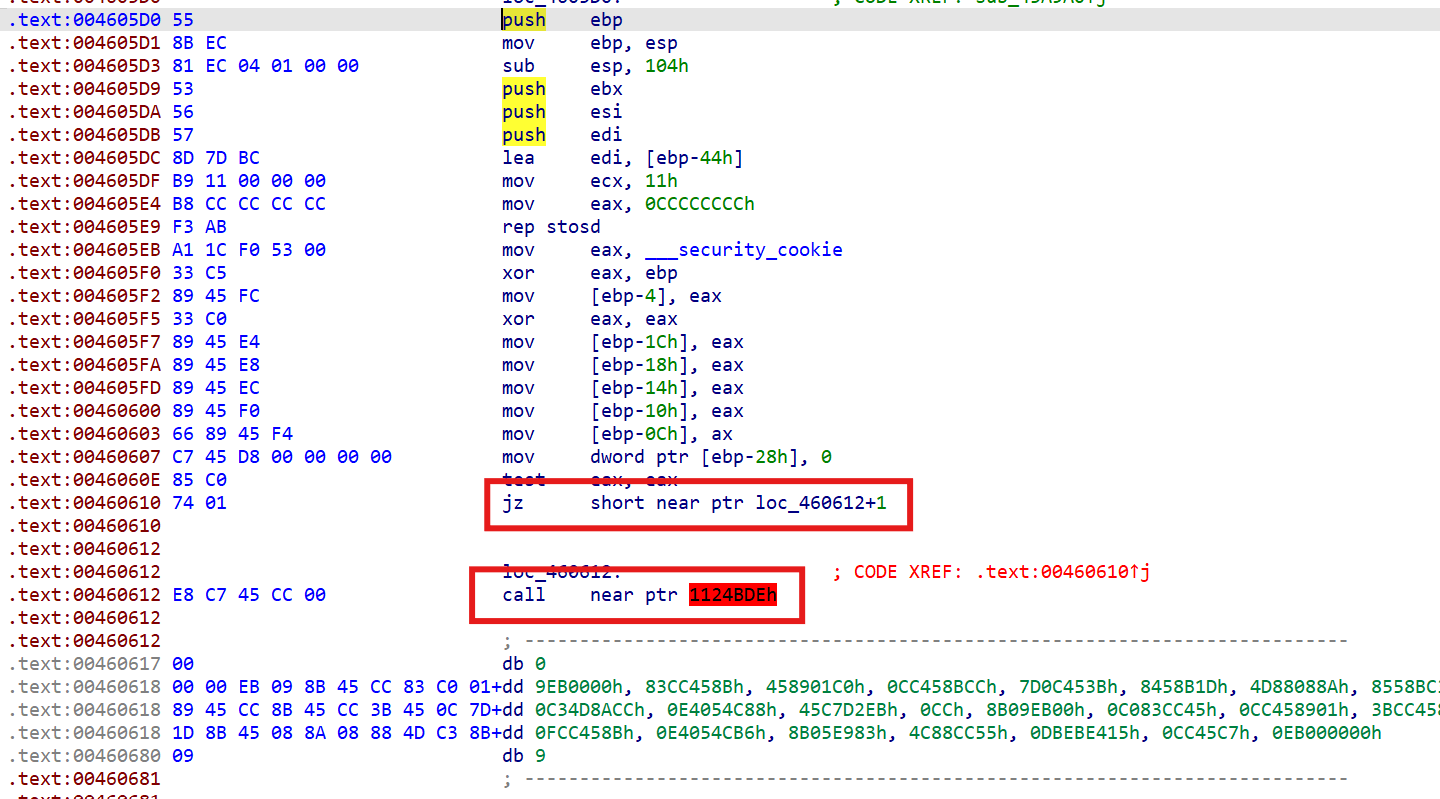
jz跳转到call,还有一堆垃圾数据
我看wp中是这样做的
跳转后没有执行E8,把E8nop掉就好了
接下来改第二个花指令
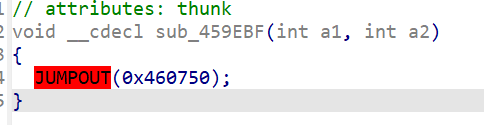
这里是jz和jnz复用,跳转,在这里依旧是E8nop掉
别忘了按P(一定在开头)
看看最后生成的函数
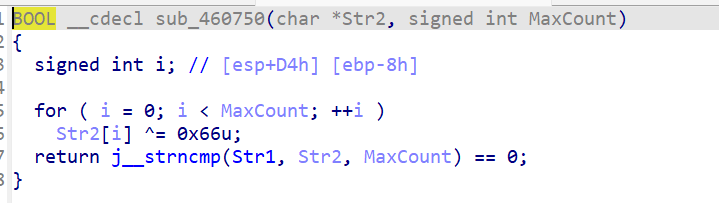
看一下str1部分的内容,并提取
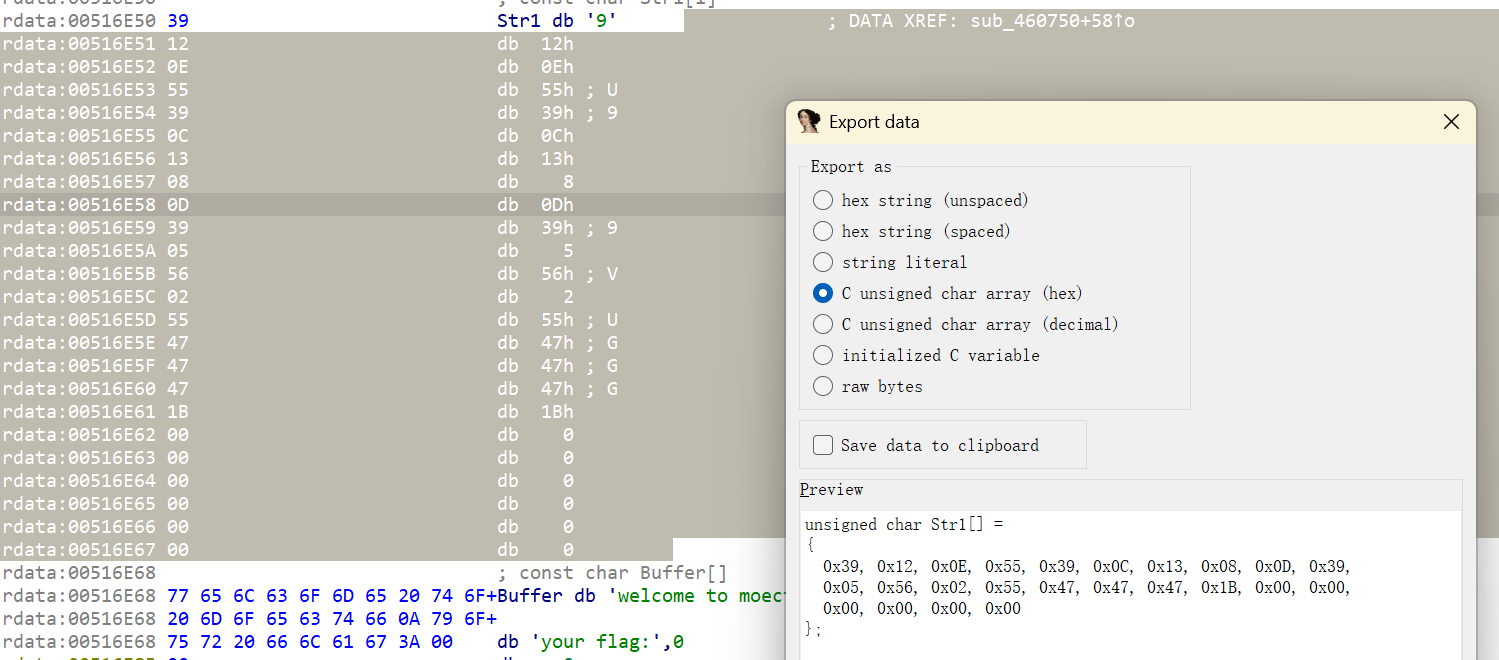
这是后十六位的内容
下面是前十六位,flag位移5(每个字节数减5)
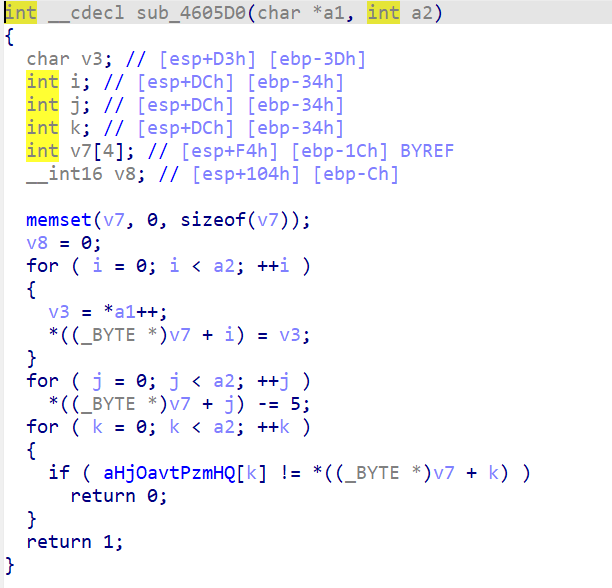
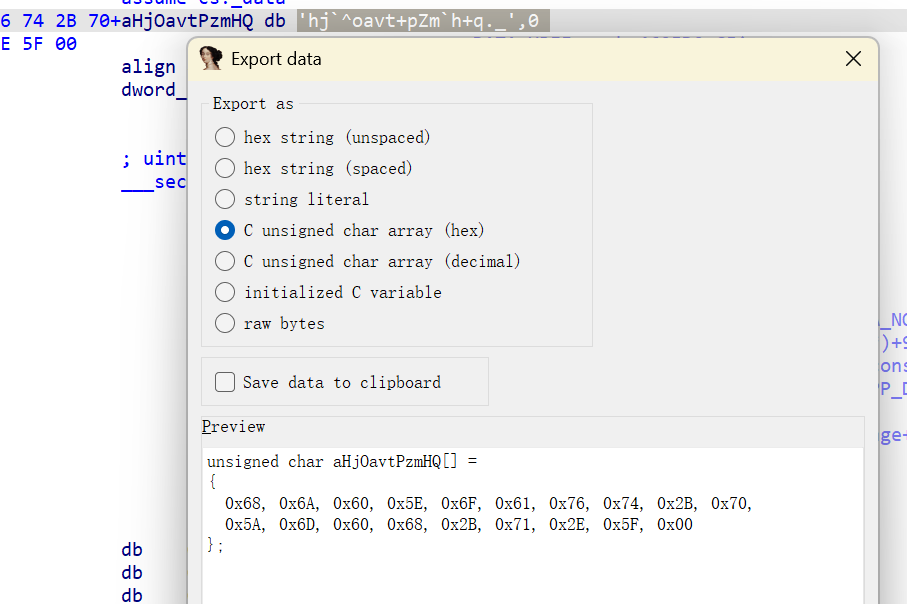
最后编写脚本,将两部分结合
1 | aH = [0x68, 0x6A, 0x60, 0x5E, 0x6F, 0x61, 0x76, 0x74, 0x2B, 0x70, 0x5A, 0x6D, 0x60, 0x68, 0x2B, 0x71, 0x2E, 0x5F] |
[HGAME 2023 week1]encode
先查壳
拖进ida中
看一下main函数的内容
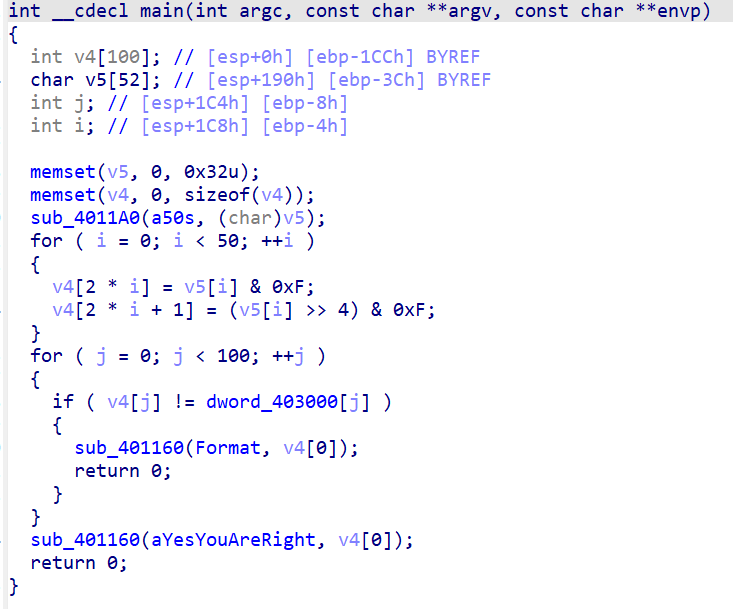
看一下逻辑
用户输入50个字符的字符串,保存到v5中,接下来拆分(拆分为两个4分位),都存储到v4中,最后将v4 的每个值与数组 dword_403000 比较,若正确返回aYesYouAreRight。
现在我们就要找到v4的内容

跟进这个函数,在里面看到v4的内容
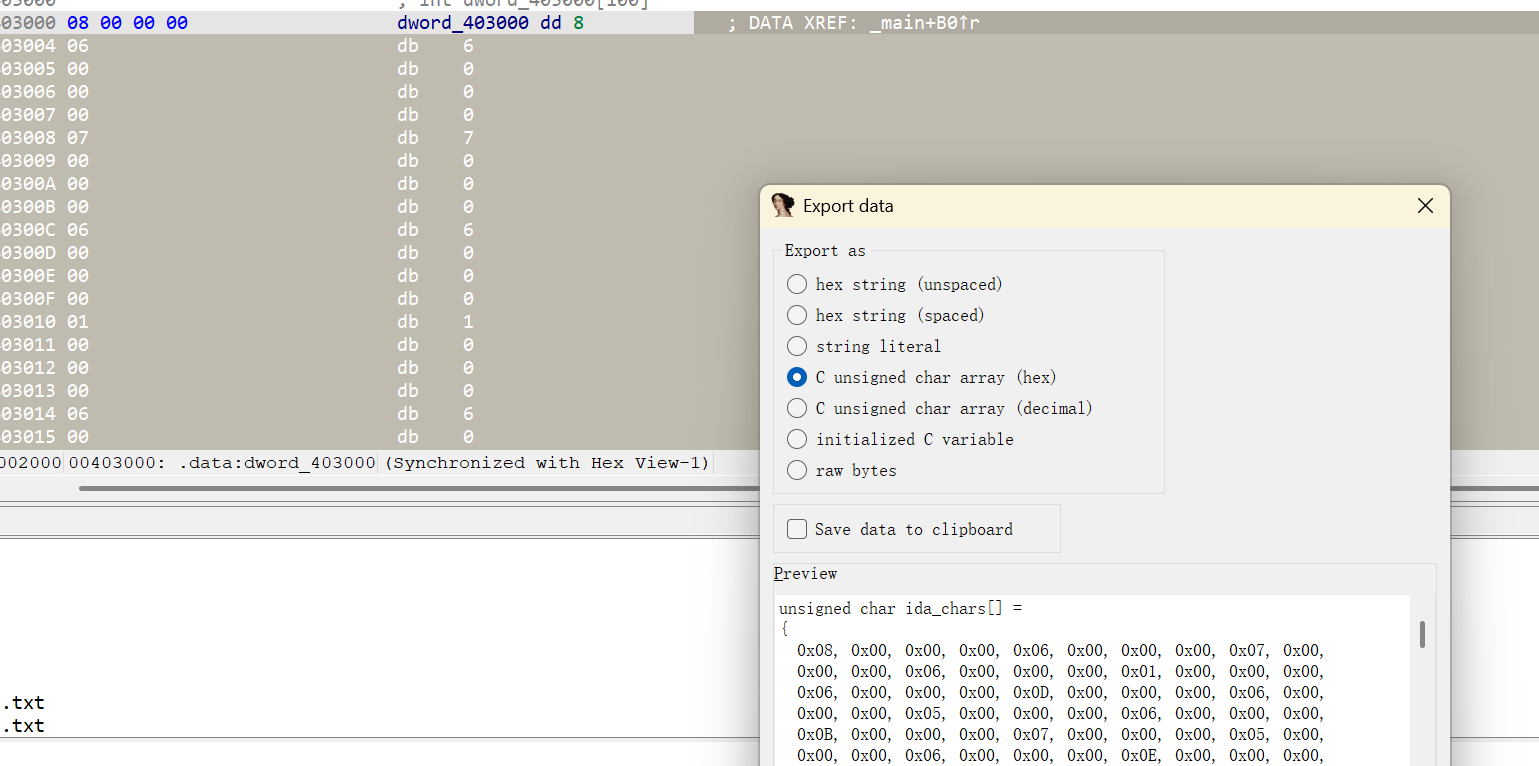
提取一下里面的内容
结合上面的逻辑,写一个脚本
1 | ida_chars = [ |
运行出结果
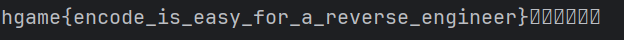
[NSSRound#2 Able]findxenny
这道题主要是考察SMC
先查壳
进去 直接查看main函数
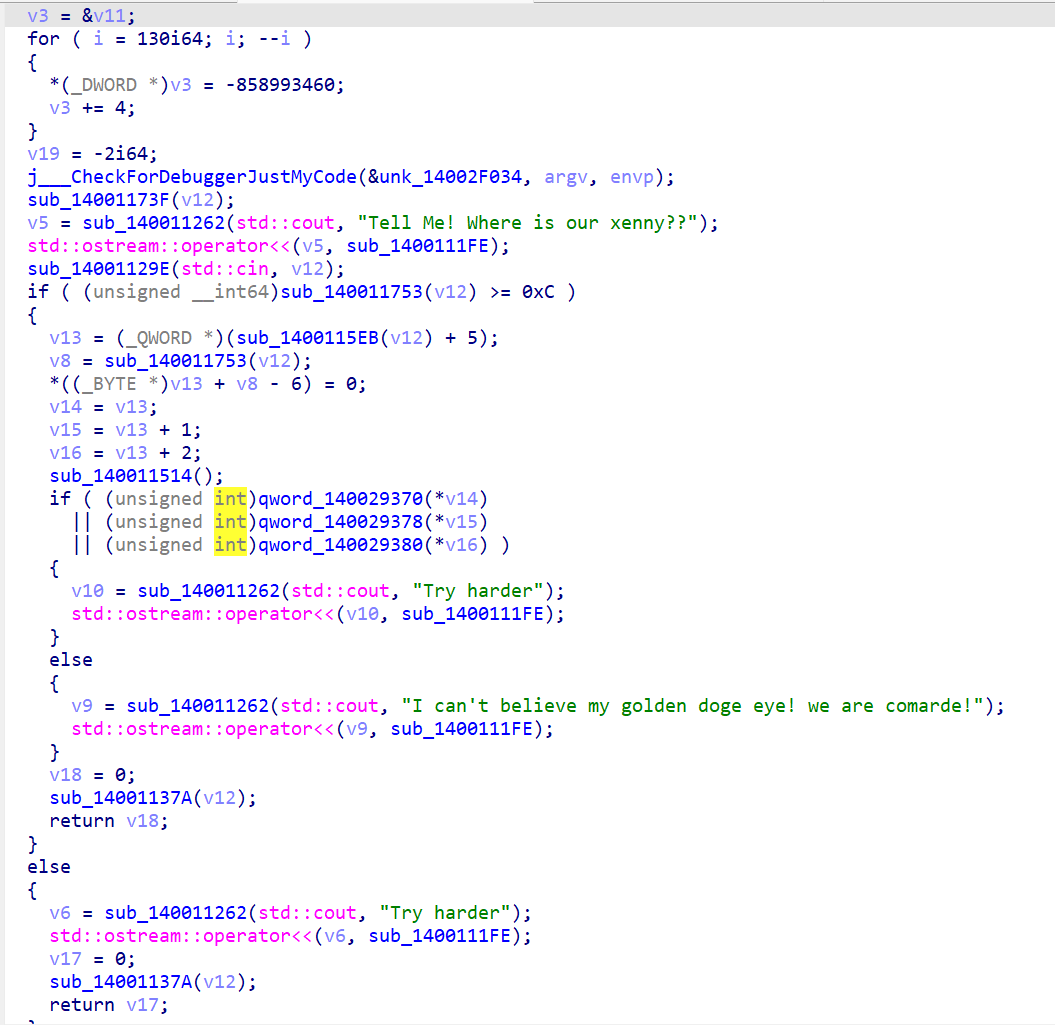
看一下具体内容
sub_140011514();这个是SMC的解密函数
跟进看一下
1 | void *__fastcall sub_140018420(__int64 a1, __int64 a2, __int64 a3) |
lpAddress = malloc(0x4Aui64); v13 = malloc(0x57ui64); v14 = malloc(0x47ui64);分配了三块内存区域。- 然后通过三个
for循环对分配的内存进行异或操作:for (j = 0; (unsigned __int64)j < 0x4A; ++j ) *((_BYTE *)lpAddress + j) = v7[j] ^ 0x5F;对lpAddress指向的内存,每个字节与0x5F进行异或(可能是一种简单的加密或解密操作,恢复或生成特定数据)。- 同理,对
v13和v14指向的内存分别与0x77、0x66进行异或。
如图中标黄部分
先尝试一下动调
在关键部分下断点
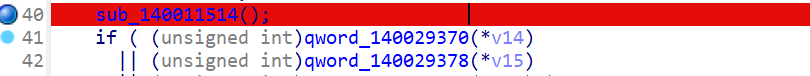
随便输入一些字符(随便输入的字符串一定要让长度大于等于0x0C(即12))
否则会直接跳出
跟进一下,看到
有的wp上按C,再按P生成函数,我试了很久都没有成功,换个方法把
算了,真的不会了